Operation Olympic Games: The first cyberweapon
- By Stavros Atlamazoglou
Share This Article

In 2010 a new era in cyberwarfare began when the Iranian scientists running the country’s covert nuclear program came to a disturbing realization: Unknown attackers – most likely the United States and Israel – had successfully inserted malware in the networks of the Natanz nuclear facility and destroyed 1,000 centrifuges critical to the covert Iranian nuclear program.
Stuxnet, as the malware became known, was the first instance in history in which a cyberweapon had substantial physical effects on a target of great geopolitical interest. Iran’s most guarded national security program had been compromised and attacked by ones and zeros. Stuxnet and the hackers behind it had just opened another phase in cyber history.
Stuxnet and Operation Olympic Games
Stuxnet was a tailored attack against the Iranian nuclear program. The creators of the cyberweapon used several unknown and unpatched vulnerabilities, known as zero-day exploits, to reach the (Siemens) programmable logic controllers that operated the centrifuges in the Iranian nuclear facility at Natanz. Once in the networks of the Iranian nuclear facility, Stuxnet modified the controllers ever so slightly in such a way that it caused the centrifuges to spin out of control and break.
The hackers designed Stuxnet to bypass most major antivirus programs by having the virus inject itself into the antiviruses’ running processes and remove itself from their sweep. Stuxnet used several different ways to spread, including a zero-day exploit that allowed it to move from one machine to another and through network file shares. The malware could also receive updates and commands from other Stuxnets.
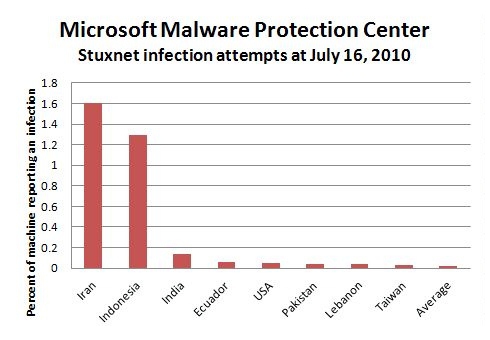
Throughout its life cycle, Stuxnet tried to remain under the radar. It went about its objective of destroying the centrifuges in a slow and incremental way that targeted and destroyed the devices over time without an obvious cause to the outsider. Indeed, the operation was so effective in that regard that the Iranian scientists were not aware of the malware until foreign cybersecurity companies picked it up. As such, Stuxnet had a psychological effect as well as a physical one, sowing distrust and doubt inside Iran’s secretive nuclear program, thereby demonstrating that such a cyberweapon can create threats on multiple levels.
Although there had been other instances of malware causing physical harm, Stuxnet was unique in its planning, engineering, resources, operational security, and technical expertise.
When Stuxnet was finally detected after more than a year of action, it had destroyed 1,000 centrifuges, which amounted to 20% of Iran’s uranium-enriching capability.
Related: The Army’s Special Forces are evolving to fight adversaries in the space and cyber domains
Cyber operations in the joint force

Stuxnet was most likely designed by committee because it was very modular. This comprehensive modularity gave the attackers the ability to replace parts of Stuxnet, as needed, and thus increase the operational security of the program. That was also the more economical approach because of the diverse set of technologies that Stuxnet targeted, including USB drives, Windows computers, and logic controllers.
A successful operation like Stuxnet requires painstaking efforts to pull off and highlights the continuously active cyber “battlefield” in which intelligence and cyber agencies have to be constantly operating in order to maintain access and thus an advantage over adversaries. As Rob Joyce, the National Security Agency’s (NSA) Director of Cybersecurity and former head of the agency’s Tailored Access Operations (TAO) unit, stated, in a lot of ways, hackers know the target networks even better than those who designed and operated them.
Moreover, Stuxnet showed that cyberweapons often go hand-in-hand and work in a complementary way with traditional military and intelligence activities. For example, although the exact method of how the attackers introduced Stuxnet on the Iranian systems remains unknown, it is likely that a human, knowingly or unknowingly, facilitated the contamination by moving data to the nuclear facility’s network. This again shows the pains that the attackers took to ensure that Stuxnet reached its target and was effective.
To be sure, cyberweapons are not cheap, and one like Stuxnet can cost hundreds of millions and take years to develop. Stuxnet came with an estimated price tag of $300 million and a development phase of at least five years. That is a lot of money and time for a one-time use weapon system. But, at the end of the day, cyberweapons are just another arrow in the policymaker’s quiver. Their deployment is governed by geopolitical considerations, and in the case of Stuxnet, secrecy and non-attributability were essential for the attackers. Stuxnet gave that and thus opened new horizons for cyber offensive operations.
Read more from Sandboxx News
- The favorite games of BUD/S instructors that SEAL candidates suffer through
- Garrett STAMP – The Marines nearly got a weird flying jeep during the Cold War
- Appearance is everything in the age of digital warfare
- F-35 versus A-10 showdown revived as new documents come to light
- SR-72? Hints of a new Skunk Works spy plane reignite rumors of a Blackbird successor
Related Posts
Sandboxx News Merch
-

‘AirPower’ Classic Hoodie
$46.00 – $48.00 Select options This product has multiple variants. The options may be chosen on the product page -

‘Sandboxx News’ Trucker Cap
$27.00 Select options This product has multiple variants. The options may be chosen on the product page -

‘Kinetic Diplomacy’ Bumper Sticker (White)
$8.00 Add to cart
Stavros Atlamazoglou
Greek Army veteran (National service with 575th Marines Battalion and Army HQ). Johns Hopkins University. You will usually find him on the top of a mountain admiring the view and wondering how he got there.
Related to: Gear & Tech, Military Affairs

British F-35s faced off against their American counterparts in rare showdown

Russian leadership tries to demonize Ukraine to make war more acceptable

The C-17 Globemaster is the Air Force’s unsung hero

Air Force is unsure of what the NGAD should do
Sandboxx News
-

‘Sandboxx News’ Trucker Cap
$27.00 Select options This product has multiple variants. The options may be chosen on the product page -

‘AirPower’ Classic Hoodie
$46.00 – $48.00 Select options This product has multiple variants. The options may be chosen on the product page -

‘AirPower’ Golf Rope Hat
$31.00 Select options This product has multiple variants. The options may be chosen on the product page -

‘Sandboxx News’ Dad Hat
$27.00 Select options This product has multiple variants. The options may be chosen on the product page
